Every time I do create a new subnet, as a best practice I create 5 security lists for each (as for now OCI does not allow me to include/remove SLs dynamically in already created subnets) so I can guarantee I can reach the maximum possible rules if it's necessary.
When you have dozens of security lists, each of them with hundreds of access rules, the OCI web interface can be really slow sometimes due to it's dynamic javascript nature. Also it don't give you filter capabilities to show, for example, all the security lists that are handling a given IP, Port or Protocol.
One of the solutions that I've found when I need to display the rules based on a custom criteria is to reformat and keep an updated copy of all my seclists data into an excel spreed. So I can use the excel columns to apply the filters I want:
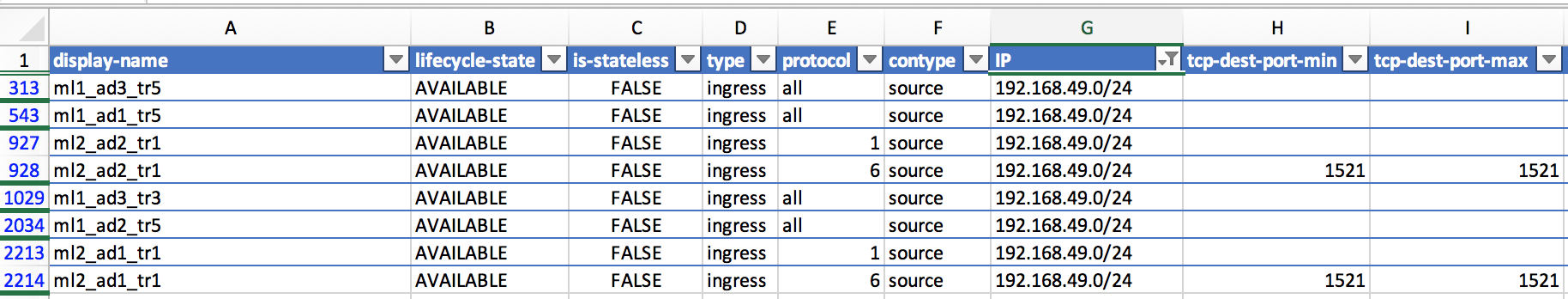
OCI interface still doesn't provide either an export button. So I created a script to make it. The code to generate the csv uses basically oci-cli and jq (lightweight and flexible command-line JSON processor). It's available at https://github.com/dbarj/oci-scripts/blob/master/oci_csv_network_seclist.sh
Before running, you must export only two shell variables specifying the Container OCID and VNC OCID which you want to generate the report:
$ ./oci_csv_network_seclist.sh OCID of compartment not specified. Please export v_compartment_ocid variable with correct value. "Prod","ocid1.compartment.oc1..aaaaaaaaqgqejobesvbinralewsj9fajs09j0jsjkjasfjaskjk0j09asfan" "Test","ocid1.compartment.oc1..aaaaaaaaaewv46xqv3n5wymaslas1nlknsna1n0nsaknr109snafkn10s0an" $ export v_compartment_ocid="ocid1.compartment.oc1..aaaaaaaaqgqejobesvbinralewsj9fajs09j0jsjkjasfjaskjk0j09asfan" $ ./oci_csv_network_seclist.sh OCID of VCN not specified. Please export v_vcn_ocid variable with correct value. "myvcn","ocid1.vcn.oc1.iad.aaaaaaaa6wlpmctr43ltu5dhgzfc3h225qymftsausf9usafu0asuf09uas9" $ export v_vcn_ocid="ocid1.vcn.oc1.iad.aaaaaaaa6wlpmctr43ltu5dhgzfc3h225qymftsausf9usafu0asuf09uas9" $ ./oci_csv_network_seclist.sh display-name,lifecycle-state,is-stateless,type,protocol,contype,IP,tcp-dest-port-min,tcp-dest-port-max,tcp-source-port-min,tcp-source-port-max,udp-dest-port-min,udp-dest-port-max,udp-source-port-min,udp-source-port-max "ml1_ad2_tr2_bkp_prd","AVAILABLE",false,"ingress","all","source","192.168.81.0/24",,,,,,,, "ml1_ad2_tr1_prd","AVAILABLE",false,"ingress","6","source","192.168.116.70/32",22,22,,,,,, "ml1_ad2_tr1_prd","AVAILABLE",false,"ingress","6","source","192.168.116.71/32",22,22,,,,,, "ml1_ad2_tr1_prd","AVAILABLE",false,"ingress","6","source","192.168.116.71/32",3389,3389,,,,,, "ml1_ad2_tr1_prd","AVAILABLE",false,"ingress","6","source","192.168.116.71/32",80,80,,,,,, "ml1_ad2_tr1_prd","AVAILABLE",false,"ingress","1","source","192.168.116.70/32",,,,,,,, "ml1_ad2_tr1_prd","AVAILABLE",false,"ingress","1","source","192.168.116.71/32",,,,,,,, (...)Have you enjoyed? Please leave a comment or give a 👍!








6 comments
Skip to comment form
Hi,
do you have the code of csv-network-security-list.sh script ? 😉
Thank you in advance.
Author
Hi Sergio, link was broken, sorry. I've already corrected that.
Regards,
RJ
Thank you very much RJ.
Have a nice day.
This was exactly what I was looking for, thanks for sharing it.
This looked really good, until I realized it's not for the newer Network Security Groups rules implementation that we use. Do you have anything similar for NSG rules, by any chance?
This is still awesome for what it is...just not QUITE what I was looking for.
I am getting error
the provided key is not a private key, or the provided passphrase is incorrect.
OCID of compartment not specified correctly. Please export v_compartment_ocid variable with correct value.